I’ve been using OPNsense firewall software now for a week on my home router, and there are quite a few things I really like so far (these will be much the same for pfSense too). Make no mistake, it was quite a steep learning curve, especially with many VLANs also being set up and getting various devices to still see each other across the VLANs. But I at least feel now that most of the devices are now safely isolated from each other.
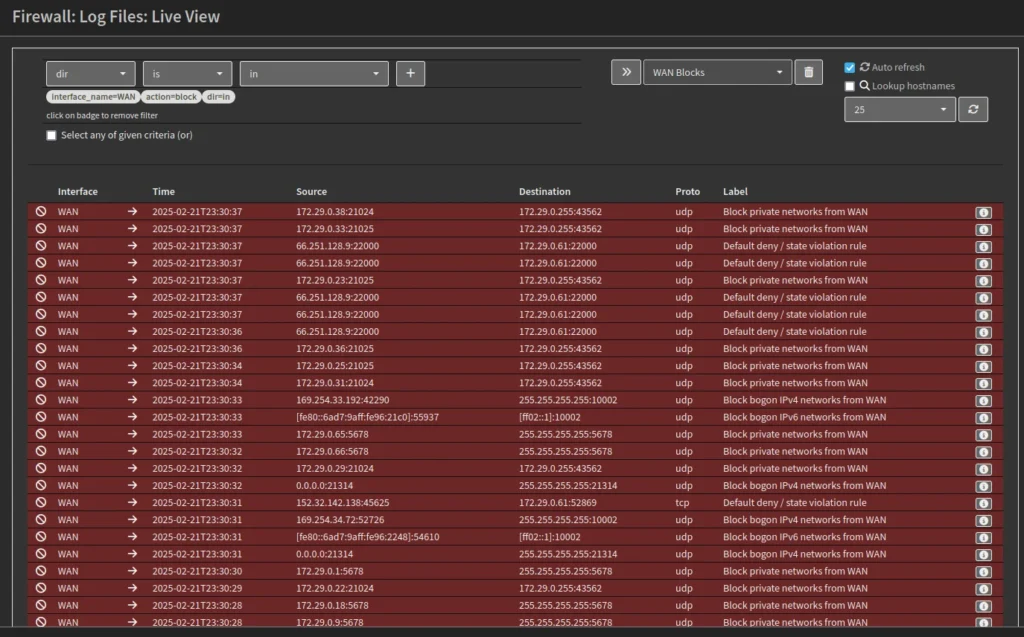
One interesting thing is the Firewall Live View where you can set filters to watch individual devices, or ports or interfaces, and also see what is being passed or blocked. For example, I use this view to also track down devices which are still configured to look for the old server IP address.
The short video clip shows you a live view of the traffic hitting the router, from the Internet, which is being blocked for being either a suspicious IP address (thanks Spamhaus DROP rules), or a private address that should not be outside, or for my domain names, anything that is not being passed through Cloudflare. No devices should be hitting my actual public IP address. But the video does show the constant barrage by scripts and bots out there.
But some other things I am liking about OPNsense so far are:
- Regular update checking and retrieval of firmware and plugin updates.
- Ability to use updated IP ban lists, Cloudflare server IP lists, etc by just specifying a link to download those lists in the background. This is combined with an Intrusion Detection system that has its rules updated daily.
- The granular control to allow just a specific device to see another specific device in a different VLAN, and only access one or more ports.
- The ability to cut off Internet access completely for a VLAN e.g for my cameras, so I know they cannot call out anywhere.
- The ability to separate my user devices, and limit their access to the network devices (I use a separate MGMT VLAN with an Ethernet cable to see those devices)
- The software is fully open source and means it will supported into the future, so I’ll get many years of use out of this versus a commercial router that just stops getting updates.
- The strict separation into VLANs has stopped the broadcasting from my cameras, Google Speakers, and media server across the whole network. Now that is confined to their own VLANs and the whole network experience is quicker.
- Aliases are a powerful way of grouping devices, network interfaces, ports, and more with their own names for easier use in firewall rules.
- Numerous plugins exist to extend functionality to even include reverse proxy functionality, DNS filtering, auto backup of configs to NextCloud, and lots more.
- The ability for a VLAN to span wired and wireless interfaces.
- The support for LAGG interfaces (combining two or more Ethernet ports to increase bandwidth and failover.
Right now I’ve closed phase one of my migration as all the basics are working. I’m going to go a bit further still next month with more tweaking and exploring of features.
Nothing is ever 100% guaranteed secure, but I can say for sure that this installation is now more than just twice as secure as my commercial Asus router was before. There are some things I still miss from my Asus router, like its traffic stats view (the way it did it), but there were also a lot of things you just could not see on the Asus router. One thing I will be exploring next month is customised or alternative dashboard views (maybe even exporting to Graphene).
But as one viewer commented, I think on the Friendica network, this is just a whole heap of fun and no-one needs any other reason to do OPNsense.