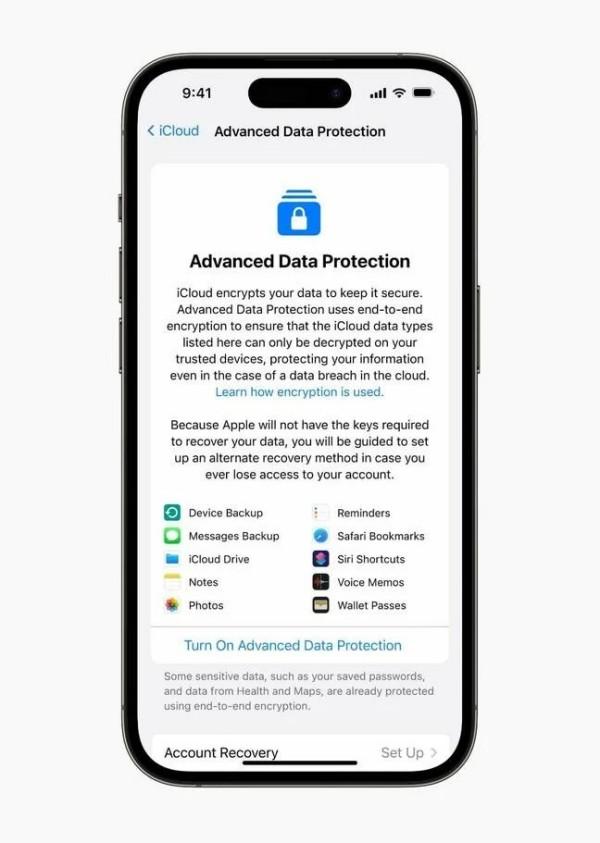
Apple has been notorious for keeping it’s own decryption keys to users’ data in iCloud, so this article required some checking. Many vendors also talk about end-to-end encryption, but mean that their server is one end of what they are talking about (which is not what we as users are thinking of).
Apple has committed to E2E encryption for 23 data categories including iCloud Backup, Photos, and Notes, among others. When users opt in to Advanced Data Protection, they will trigger the deletion of encryption keys stored in the cloud that gave Apple access to their data.
Messages in iCloud under standard data protection are E2E encrypted unless iCloud Backup is enabled. In that case, the encryption key gets stored with the backup to facilitate data recovery. With Advanced Data Protection, that exception disappears – everything in the iCloud Backup, including the encryption key, is protected.
Some iCloud metadata and usage information will remain accessible to Apple – still encrypted, but with keys under Apple’s control. That includes file modification timestamps and checksums for file and photo data – hashes that may have some utility for identifying known illegal images or other law enforcement inquiries.
Data from iCloud Mail, Contacts, and Calendar apps will also not be fully protected. This is because the default for mail and calendaring system is non-encrypted open text. Seems unbelievable, but the easy answer is it is too complicated for most average users to know how to set up encryption for their e-mail… Yes, I know, Proton Mail and Tutanota are not difficult…
Sounds also like Yubikey and similar hardware key support is also coming.
What we don’t know yet, is what impact this may have on relatives inheriting deceased users’ account data. My guess is, if it is secure and you don’t have the decryption password, that data is gone (the way it should be if it is secure).
See https://www.theregister.com/2022/12/08/apple_encryption_icloud/
#technology #Apple #privacy #iCloud #E2EE