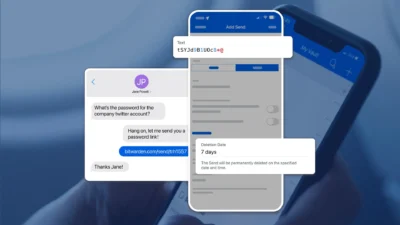
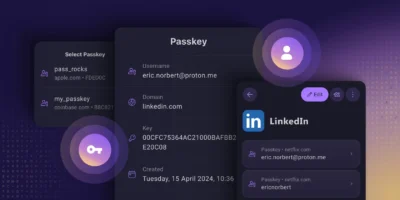
7 password rules to live by in 2024, according to security experts – No, frequent changes not one of the rules

If you really want to get deep into the details of digital security, read the four-volume Digital Identity Guidelines from the National Institute of Standards and Technology (NIST). It’s a massive document, and much of […]